 There is an adage that has become all too common when dealing with a potential data breach: it’s not a matter of if, but when. Sad, but ultimately true. When it comes to cybersecurity for your (or your client’s) business, you can never be too careful. Engaging in a risk assessment for the business is essential to understand an appropriate risk threshold and implementing an incident response plan should a data breach occur. A data security program is absolutely essential, and must be reasonable and adequate. This is a lesson the now defunct LabMD discovered the hard way in its enforcement dance with the FTC, but perhaps for all the wrong reasons.
There is an adage that has become all too common when dealing with a potential data breach: it’s not a matter of if, but when. Sad, but ultimately true. When it comes to cybersecurity for your (or your client’s) business, you can never be too careful. Engaging in a risk assessment for the business is essential to understand an appropriate risk threshold and implementing an incident response plan should a data breach occur. A data security program is absolutely essential, and must be reasonable and adequate. This is a lesson the now defunct LabMD discovered the hard way in its enforcement dance with the FTC, but perhaps for all the wrong reasons.
The LabMD case is a strange and winding road to say the least, but a little background is helpful in providing context. LabMD was a medical laboratory that performed diagnostic testing for cancer patients, which made it subject to Health Insurance Portability and Accountability Act (HIPAA) regulations. Although LabMD implemented a data security program to implement those regulations, the billing manager at LabMD installed a peer-to-peer file sharing program (the now defunct LimeWire) in violation of that policy that exposed a file containing the personal health information of over 9,300 patients. Not good. A third-party data security company called Tiversa Holding Company (“Tiversa”) evidently downloaded the file containing that information through LimeWire, and used that information to solicit LabMD to use its services to remediate the problem. Really not good. After repeatedly refusing to engage Tiversa, Tiversa ultimately delivered the contents of that file through a separate entity to the FTC so that Tiversa would not be linked to the disclosure due to a pending acquisition (yep, you read that correctly). Apparently, hell hath no wrath like a data security company scorned.
Ultimately, the FTC thoroughly investigated LabMD and, in 2013, issued an administrative complaint alleging that LabMD “failed to provide reasonable and appropriate security for personal information on its computer networks.” Although an administrative law judge initially dismissed the case, the long and the short of it, without going into too much procedural detail, is that the FTC was eventually able to issue an order “vacating the ALJ’s decision and enjoining LabMD to install a data-security program that comported with the FTC’s standard of reasonableness.” LabMD petitioned the 11th Circuit to review the order and moved to stay it over the FTC ’s objections. In sum, the FTC pressed LabMD (no longer a going concern at this point, due in no small part to the weight of the FTC action) to implement a very broad and incredibly vague order. If this is sounding problematic to you, join the club.
Billables Are Not The Same As Cash Flow. Here’s Why That’s Important.
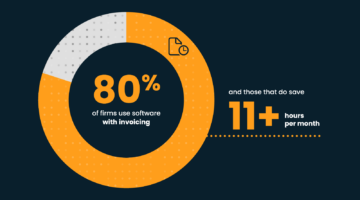
Findings from the MyCase 2025 Legal Industry Report.
This past July, reason prevailed and the 11th Circuit ruled that the FTC went too far and held the FTC order unenforceable. Ultimately, the court found that the FTC order unenforceable because it was “founded on LabMD’s failure to act.” More specifically, the court stated that:
[i]n the case at hand, the cease and desist order contains no prohibitions. It does not instruct LabMD to stop committing a specific act or practice. Rather, it commands LabMD to overhaul and replace its data-security program to meet an indeterminable standard of reasonableness. This command is unenforceable….
As a result, the FTC’s enforcement in this area will never be the same.
What does this ruling mean with respect to your company (or your client)? Well, it actually means a lot. Here are the three biggest takeaways from my perspective:

Why Some Firms Are Leading The Market With Generative AI
A culture of innovation with strategic AI like Lexis+ AI is revolutionizing law firms by boosting efficiency and deepening client relationships.
1. The FTC Still Has Authority Over Data Security Compliance under Section 5 of the FTC Act. Whether you like it or not, the FTC’s authority under Section 5 of the FTC Act to protect consumers against “unfair acts or practices” still applies to data security programs. The 11th Circuit ruling did not upset the holding set forth in FTC v. Wyndham Worldwide Corporation, confirming the FTC’s regulatory authority under Section 5 of the FTC Act. Ignore the FTC at your own peril.
2. Future FTC Enforcement Will Need to Be a Lot More Specific. Notwithstanding the foregoing, there is a plus side — the FTC will be required to address specific acts or practices regarding data security (or lack thereof) in any enforcement proceeding and eventual order. Broad-brush, vague orders requiring “reasonable” data security standards will no longer suffice, so the FTC will need to be more targeted in the future.
3. “Reasonable and Appropriate Security Measures” Will Need to Be Specific, Too. Let’s face it — you absolutely need a data security program, but it will need to be reasonable, consistent with an acceptable level of risk tolerance for the company, and comprehensive enough to adequately cover such risk. If a company implements a reasonable and appropriate security program and can prove-up its compliance with such a program, the potential for an FTC investigation and subsequent enforcement order will be minimized. You can’t avoid FTC jurisdiction, but you can avoid being on their radar.
The need for a proper data security program has never been more clear. The FTC is not going to take this 11th Circuit decision sitting down, and will attempt to define “reasonable and appropriate standards” in future actions or guidance. Remember — it’s not a matter of if, but when a company will need to address potential data breaches. If you don’t take the time to heed these takeaways and implement and update a reasonable and appropriate security program, the same adage may apply to the FTC looking at your company (or your client), and that’s not a place that your company (or your client) wants to be — just ask LabMD.
 Tom Kulik is an Intellectual Property & Information Technology Partner at the Dallas-based law firm of Scheef & Stone, LLP. In private practice for over 20 years, Tom is a sought-after technology lawyer who uses his industry experience as a former computer systems engineer to creatively counsel and help his clients navigate the complexities of law and technology in their business. News outlets reach out to Tom for his insight, and he has been quoted by national media organizations. Get in touch with Tom on Twitter (@LegalIntangibls) or Facebook (www.facebook.com/technologylawyer), or contact him directly at [email protected].
Tom Kulik is an Intellectual Property & Information Technology Partner at the Dallas-based law firm of Scheef & Stone, LLP. In private practice for over 20 years, Tom is a sought-after technology lawyer who uses his industry experience as a former computer systems engineer to creatively counsel and help his clients navigate the complexities of law and technology in their business. News outlets reach out to Tom for his insight, and he has been quoted by national media organizations. Get in touch with Tom on Twitter (@LegalIntangibls) or Facebook (www.facebook.com/technologylawyer), or contact him directly at [email protected].